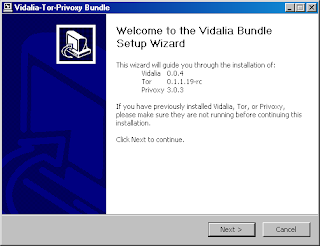
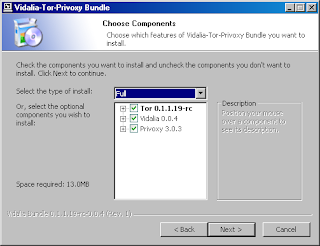
i am back,Now a days i have seen many of my friends worrying about virus attacks on their systems,So i thought to do something in order to solve or even try to do this.
here i provide some anti virus software and their needs
NORTON ANTI VIRUS

Features
* Improved performance delivers faster scans NEW
* One click access to expert support NEW
* Works quietly in the background. NEW
* Network mapping provides a view of your home network. NEW
* Detects and removes spyware and viruses
* Blocks spyware and worms automatically
* Protects email and instant messaging from viruses
* Prevents virus-infected emails from spreading
* Rootkit detection finds and removes hidden threats
* Includes protection updates and new product features as available throughout the renewable service period *
SYSTEM REQUIREMENTS
Windows Vista® Home Basic/ Home Premium/Business/Ultimate**
Windows® XP with Service Pack 2 Home/XP Pro/XP Media Center Edition
* 300MHz or higher processor
* 256MB of RAM
* 300MB of available hard disk space
** Must meet minimum Windows Vista operating system requirements.
Email scanning supported for POP3 and SMTP compatible email clients.
Supported instant messenger clients:
* AOL® – 4.7 to 5.9
* Yahoo!® – 5.x and 6.x
* Microsoft® – 6.0 or higher
* Trillian™ – 3.1 or higher
AVAST ANTI VIRUS:

Features:
* Standard Shield — Real-time protection
* IM shield — Instant Messenger protection
* P2P shield — P2P protection
* Internet Mail — E-mail protection
* Outlook/Exchange — Microsoft Outlook/Exchange protection
* Web Shield — HTTP protection (localtransparent proxy)
* Script blocker — script checker (Pro version only)
* Network Shield — basic protection against well-known network worms. Acts as a lightweight Intrusion Detection System
* Audible alarms — vocal warnings such as "Caution, a virus has been detected!"
* Boot-time scan — through the program interface, a user can schedule a boot-time scan to remove viruses that load during Windows startup and are therefore difficult to remove.
AVG ANTIVIRUS

All-In-One Protection
* Anti-Virus protects from viruses, worms and trojans
* Anti-Spyware protects from spyware, adware and other malicious programs
* Anti-Spam filters spam and protects against phishing attacks
* Firewall protects from hackers
Features
* All-in-one, easy to use protection - install and forget
* New program versions and updates automatically applied for free for the duration of your subscription
* Quality proven by all major antivirus certifications (VB100%, ICSA, West Coast Labs Checkmark)
* 24/7 technical support provided at no extra cost
* Improved virus detection based on better heuristics and NTFS data streams scanning
* Unique automatic threat-removal anti-spyware engine
* Automatic firewall profile switching for improved security and usability
* 100% virus detection — AVG’s scanning engine has received numerous awards for its excellent detection of “in the wild” viruses, including the VB100% award. Its unique combination of detection methods provides full protection against viruses, worms and trojans.
* Cutting-edge anti-spyware technology — Using the latest state-of-the-art detection technology, AVG detects spyware, adware, DLL-trojans, keyloggers, and much more. Malware hidden in data streams, archives, or the Windows registry is also detected.
* Full on-access protection — The powerful AVG Resident Shield provides maximum protection by scanning every file opened, executed, or saved. It also prevents the opening or executing of infected files.
* Flexible intelligent scanning — The AVG Resident Shield can include/exclude files from being scanned based on individual file extensions and can handle exceptions for potentially unwanted programs such as adware.
* Full e-mail protection — AVG checks every e-mail sent or received, providing full protection from e-mail-borne threats. AVG supports all leading e-mail clients, including MS Outlook, The bat!, Eudora, and all other SMTP/POP3-based e-mail clients, such as Outlook Express. Encrypted connections using SSL are also supported.
* E-mail spam and phishing filtering — AVG checks every e-mail received, using the latest technology and up-to-the-minute spam signatures to ensure maximum detection rates for spam and phishing attacks.
* Automatic threat handling — AVG can automatically heal or remove infected files and other threats such as trojans, worms and spyware.
* Control over all network access — The AVG Firewall monitors all communication to and from the computer, blocking external attacks and preventing trojans from exporting confidential data. The AVG Firewall configuration wizard automatically creates access rules for all popular software. In addition the firewall can switch profiles automatically, based upon the current conection type, ensuring seamless changeover for notebooks.
* Powerful scheduling — AVG automatically provides recommended daily schedules for scanning and updating, and also allows you to create custom-scheduled events.
* Multiple language support — No need to buy a special language version.
Supported platforms
Platform
[Operating System] AVG Internet Security
MS Windows 98 * Yes
MS Windows Me * Yes
MS Windows NT * Yes
MS Windows 2000 Yes
MS Windows XP Yes
MS Windows XP Pro x64 Edition Yes
MS Windows Vista Yes
MS Windows Vista x64 Edition Yes
MS Windows NT Server 4.0 No
MS Windows 2000 Server No
MS Windows 2003 Server No
MS Windows 2003 Server x64 Edition No
Linux i386 No
FreeBSD No
Symbian No
Platform
[Application]
MS Exchange Server 5.x No
MS Exchange Server 2000/2003 No
MS Exchange Server 2007 No
Kerio MailServer 5/6 (MS Windows) No
Kerio MailServer 5/6 (Linux i386) No
Lotus Domino (MS Windows) No
Lotus Domino (Linux i386) No
PostFix No
QMail No
SendMail No
Exim No
Important notice
* * Operating systems marked with an asterisk (MS Windows 98, MS Windows ME and MS Windows NT) will only be supported until August 2008.
* Anti-Spyware on-access scanner is available only on Windows 2000 SP4 + Update Rollup 1, Windows XP SP2, Windows XP Pro x64 Edition SP1 and Windows Vista/Vista x64 Edition.
Free Customer Support
* AVG's world-class product support is provided at no extra cost to all registered AVG customers.
* 24/7 technical support by e-mail
* FAQ and online documentation
* Up-to-the-minute updates available "around-the-clock" as AVG virus experts react rapidly to new and emerging threats. High speed delivery via worldwide networks guarantees maximum protection levels for users.
Minimum System Requirements
* Windows Vista, Windows XP, Windows 2000, Windows NT, Windows Me, Windows 98. Note: AVG home and small office products do not have support for server operating systems (Windows NT Server, Windows 2000/2003 Server, etc.). If you are interested in server protection, please continue with Small Business solutions.
* 1,2 GHz Processor
* 70 MB free hard drive space
* 256 MB RAM
Licensing
* AVG Internet Security requires 1 license per computer and can be purchased in packs for 1,2,3 and 5 computers.
* Licenses can be purchased for 1 or 2 years.
* Each license includes all program and database updates and full technical support for the license duration.
* For more information and special licensing please contact Sales Support.